Cryptographic Processes
- Process of converting ordinary plain text into unintelligible text and vice-versa.
- The science of encrypting and decrypting information is called cryptography.
- The primary purpose of cryptography is to making difficult for unauthorized third party to access and understand private communication between two parties.
- Encryption uses complex algorithms to convert the original message, or cleartext, to an encoded message, called ciphertext
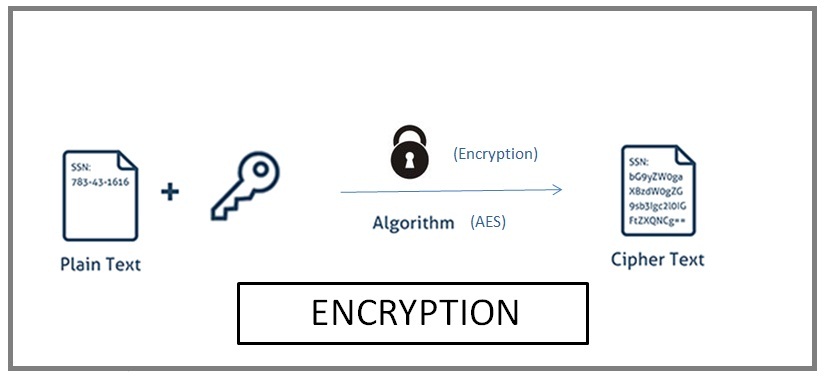
What is Encryption?
- Method which information is converted into secret code that hides the information’s true meaning.
- So only authorized parties can understand the information
- Here it is using a complex algorithm to convert an original message, or cleartext, to an encoded message
- We called it ciphertext
- Formulas used to encode and decode messages are called encryption algorithms, or ciphers
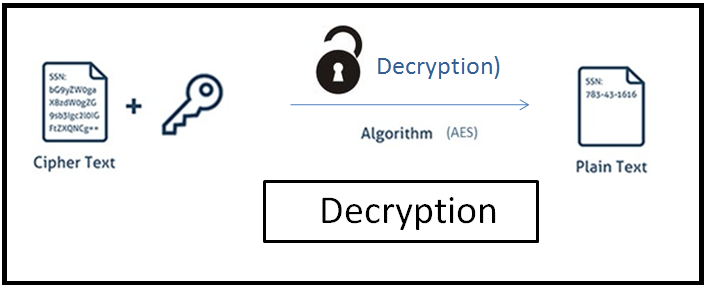
What is Decryption?
- Decryption is a process that transforms encrypted information into its original format.
- This Transforms information from unreadable format
- called ciphertext to its original format which we called plaintext .
- So this is inverse process of encryption.
- That means producing cleartext from ciphertext.
Importance of encryption
- Privacy:
- Encryption ensures that no one can read data except the rightful data owner.
- This prevents attackers who is trying to read sensitive data.
- Security:
- Encryption helps prevent data breaches.
- If your device is lost or stolen and its hard drive is properly encrypted, the data on that device will still be secure.
- Similarly, encrypted communications enable the communicating parties to exchange sensitive data without leaking the data.
- Data integrity:
- Encryption also helps prevent malicious behavior such as on-path attacks.
- When data is transmitted across the Internet, encryption ensures that what the recipient receives has not been altered with on the way.
- Authentication:
- This allows users be sure that they are connected to the real website
Disadvantages of encryption
- in some situations, encryption can keep the data’s owner from being able to access the data as well.
- Key management is one of the biggest challenges of building an enterprise encryption and it adds extra complexity to the backup and restoration process also.
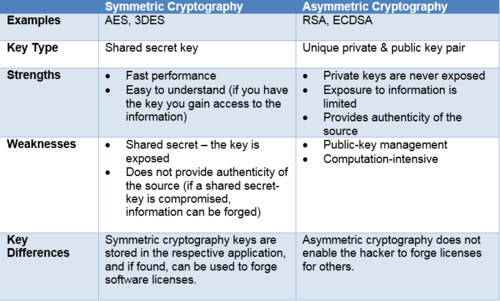
Symmetric Encryption (Secret Key Cryptography)
- The two main kinds of encryption are symmetric encryption and asymmetric encryption.
- In symmetric encryption, there is only one key, and all communicating parties use the same (secret) key for both encryption and decryption.
- The majority of the sensitive data sent in an SSL session is sent using secret key cryptography.
- One of the major problems with secret key cryptography is the logistical issue of how to get the key from one party to the other without allowing access to an attacker.
Asymmetric Encryption (Public Key Cryptography)
- Asymmetric encryption is also known as public key encryption.
- In asymmetric, or public key, encryption, there are two keys: one key is used for encryption, and a different key is used for decryption.
- Public key cryptography requires extensive computations, making it very slow. It is therefore typically used only for encrypting small pieces of data, such as secret keys, rather than for the bulk of encrypted data communications.
Comparison Between Secret Key and Public Key Cryptography
Types of encryption
- Cloud storage encryption
- This service is offered by cloud storage providers.
- This is use when data or text is transformed using encryption algorithms and is then placed in cloud storage
- End-to-end encryption
- Also known as E2EE.
- Mostly this is use in Messaging apps such as Messenger , WhatsApp
- HTTPS
- This enables website encryption by running HTTP over the SSL/TLS protocols.
- To enable a web server to encrypt all content that it sends, a public key certificate must be installed.
What is an encryption algorithm?
- An encryption algorithm is the method used to transform data into ciphertext.
- An algorithm will use the encryption key in order to alter the data in a predictable way.
Common encryption algorithms
Symmetric encryption algorithms
- AES
- Advanced Encryption Standard – (normally believe AES is resistant to all attacks which tries to decode messages (using all possible combinations of 128, 192, or 256-bit cryptosystems)
- DES
- Data Encryption Standard (is an outdated symmetric key method of data encryption. works by using the same key to encrypt and decrypt a message, so both the sender and the receiver must know and use the same private key)
- 3-DES
- Triple DES -(Triple DES uses three single 56-bit keys each. )
Asymmetric encryption algorithms
- RSA
- RSA is popular due to its key length and therefore widely used for secure data transmission.(Many protocols, like Secure Shell (SSH), OpenPGP, Secure/Multipurpose Internet Mail Extensions (S/MIME) and Secure Sockets Layer (SSL)/TLS, rely on RSA for encryption and digital signature functions)
- DH
- Diffie–Hellman

